
Phishing is a form of a cyberattack when hackers pose as institutions or authoritative figures to steal people’s credentials, passwords, and banking information via emails, phone calls, or SMS messages.
Such information can provide access to company or individual financial accounts and other sensitive data, making it valuable for future scams, monetary theft, and extortion.
Disclaimer: If you suspect you might be dealing with a phishing attempt via email or SMS – do not click any links or open any files until you are sure it’s legit.
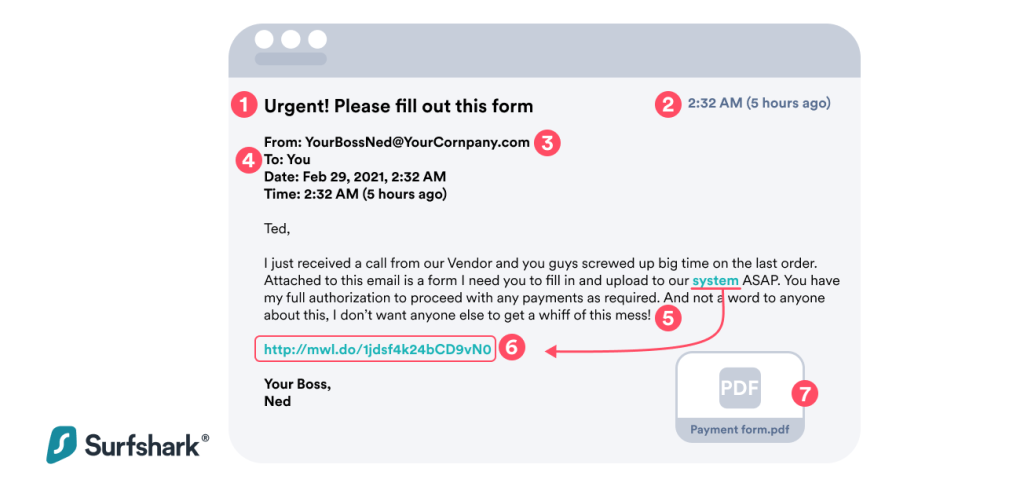
Phishing example: most common indicators of any phishing attempt
If you’re wondering whether someone’s trying to phish you, there are signs to look out for. Here’s a BEC (Business Email Compromise) spear-phishing email as an example to illustrate the most common indicators of a phishing attempt:
-
- Subject line
- Is there a sense of urgency right off the bat? Phishers want you to act without thinking. The most common sign of any BEC or phishing attempt is the sense of urgency or time running out.
- Does the subject match the content? Sometimes the subject line does not match the text inside. That’s a red flag!
-
- Date & time
- Is the time sensible? Even if urgent, would you have received such an email from your boss outside of work hours?
- Do you often receive emails during weekends? If not, that’s another possible suspect point added to your list.
-
- From
- Do you recognize the person writing to you? Are they your customer or from your company? Is their tone of voice strange or different?
- Should the person be writing to you? Is Ned your direct supervisor? Do you communicate often?
- Is the email domain correct or suspicious? Note that the domain name is “YourCor-npany,” not “YourCompany.” If you notice this, don’t even read the email further.
- Does the email come with an attachment from someone you don’t know? If you receive an attachment from anyone unfamiliar to you, DON’T OPEN IT.
- Do the “from” and “reply to” email addresses match? Sometimes pressing the reply button may prompt you to use a different email address than the one you’ve received from. This is a major red flag!
-
- To
- Did you receive a personal email in a cc chain?
- Do you know the people that were cc’d? Sometimes a full list of random people receiving one such email is an indicator of a phishing scam.
-
- Text
- Does the text have grammar mistakes? Is it poorly structured, riddled with errors?
- Does the text make sense? Is the request sensible/relevant to your work?
- Does it promise consequences? Phishing emails most often prey on people’s emotional susceptibility. Does the email make you feel like you’ve messed up?
- Does the text mention payments or anything financial? Anything related to finances in an already suspicious text is a major red flag.
- Does it ask you to click on a hyperlink? Would your boss or colleague send you a hyperlink to somewhere you often access yourself?
- Does the urgency theme continue in the text?
- Does the text ask you to keep the matter private? The likelihood of a successful phishing attack increases if you don’t talk to anyone about it.
-
- Hyperlinks
- Does the hyperlink lead to a suspicious domain? Hover your mouse over the link and see if it’s a real link, something quite random like http://mwl.do/1jdsf4k24bCD9vN0 is a major warning sign.
- Is the hyperlink correct? Like with the domain name, phishers often create websites with typos to lure you into clicking the link. Especially look for subtle details like “yourcompany.co” vs. “yourcompany.com” or “http://yourcompany.com” vs. “https://yourcompany.com”.
-
- Attachment
- Does the file type match the email context? The most common attachments are malware-riddled windows.exe files that hardly anyone would send via email in a business setting. However, docs, excel sheets, PDFs, and anything besides .txt can be infected too.
- Does the email author ever send you attachments? Have you ever received a PDF from Ned? There’s a first time for everything, but hopefully not when it comes to phishing.
- Does the email come with an image? Phishing emails may contain 1×1 pixel images (a.k.a, tracking pixels) that your computer automatically downloads when you open an email.
In short, the most common phishing indicators can be summarized in the following points:
- Sense of urgency. Social engineers want you to act without thinking and therefore might urge you to do something as fast as possible.
- Unknown or suspicious senders. If you don’t know or recognize the sender of the email, or their address seems fishy, it might indicate you are being phished.
- Grammar mistakes. If you receive an email from an Institution or someone from work and it’s full of grammar mistakes, always double-check if it’s legit.
- Riddled with hyperlinks. Hyperlinks are easily masked and can lead to malware or clone websites that can infect your device or attempt to steal your credentials.
- Finance related. Many phishing emails, especially BECs, have something to do with finances or financial requests. Be extra cautious when dealing with them.
- Out of context attachments. Be careful when receiving emails with attachments, especially if they come from unknown senders or have windows.exe files. And remember: all attachments besides .txt files can be infected with malware.
- CC chains. If you receive a “personal” email and it’s a part of a huge cc chain with people you don’t know, then you’re likely dealing with a phishing email.
Symantec’s report also warns against subject lines that include the following keywords:
- Urgent
- Request
- Important
- Payment
- Attention
For phishing in general, KnowBe4 noted that the most common phishing email subject lines in Q4 2020 referred to health and stimulus benefits (in the wake of COVID) while also using big brand names like Twitter, Google, Microsoft, Zoom, and Amazon.
From these findings, it becomes quite clear that social engineering preys on two things:
- People’s emotional susceptibilities, especially to urgency and authority.
- Recognizable big brand names that often send email notifications and promotions.
Different types of phishing
Above I gave a single example of a BEC email, but phishing comes in many forms. Below are ten different types of phishing techniques most commonly used by social engineers.
Spam phishing

Spam phishing is one of the oldest forms of phishing that’s been around the internet for decades. Hackers use text like the (in)famous “Nigerian Prince” and send millions of spam emails to people worldwide.
Spear phishing

Spear phishing is a form of phishing when a threat actor targets a particular person as, in the example above. It can prove extremely devastating because hackers use people’s personal information for leverage when orchestrating such attacks. It’s best to keep information about yourself private. General advice is to avoid putting data that can put you in danger of phishing on social media platforms like Instagram, Facebook or Twitter.
URL phishing

We’ve discussed an element of URL phishing in the above example, but it is essentially a form of phishing that’s carried out by spoofing domain names. The most common cases of this kind of URL spoofing are confusing letters like “r” and “n” with “m,” “.co” with “.com,” and so on.
Smishing

SMS phishing, or smishing, happens when you receive a phishing text message via phone. These are often scams asking to click certain URLs (You’ve won a prize!) or otherwise provide personal information.
Vishing

Vishing, or voice phishing, is similar to smishing, only that it is a scam over a phone call. The person calling you might pretend they are from an authoritative institution or lie about your family member being in trouble.
Often vishers will try to lure your sensitive or financial information like an SSN (Social Security number) or credit card number. Their main tactics often revolve around being obscure about the details or mumbling in response to your questions.
BEC

As illustrated above, a BEC (Business Email Compromise) is a form of phishing when a threat actor poses as an employee’s boss or a superior. This type of attack aims to leverage a person’s sensitivity to authoritative figures and manipulate them into wiring company funds or exposing access credentials to the attackers.
Whaling

Whaling is a spear phishing attack explicitly aimed at CEOs, CMOs, COOs, and other top-level executives. Such attacks’ usual purpose is to have high-level employees reveal confidential information that the attackers can later use for money extraction or extortion.
Angler phishing
Angler phishing emerged on social media, especially Twitter after hackers began using fake brand accounts to respond to users’ comments or complaints. Often, attackers phish for personal information and credentials they can later use to cheat or blackmail the individual.
SEO phishing

SEO phishing, or a search engine attack, is a more sophisticated form of phishing when threat actors use search engine optimization to promote their phishing websites organically. These sites often promise discounts, free items, and fake deals to make people share personal information and credit card details.
Tabnabbing

Tabnabbing preys on people who have many tabs open at the same time. During the attack, the phishing website imitates a legitimate site and opens a new tab in a user’s browser (e.g., Gmail), prompting them to log in by using their credentials. This way, the attackers can gain easy access to a user’s sensitive information.
How to avoid the damage phishing can cause
Successful phishing scams can be deadly for both individuals and organizations. An average company-wide data breach costs an average of USD 3.86 million, while a successful attack on an individual can cost them their wellbeing.
Apart from learning how to avoid getting phished, there are additional measures you can take to prevent successful phishing attacks from hurting you.
In other words, if your credentials get stolen, there is not much you can do to get them back. However, you can minimize the damage by doing the following:
- MFA – Multi-Factor Authentication acts as a second security layer to your password if your credentials ever get stolen. It is applicable for both organizations and individuals, as it can save you from personal losses or company-wide data breaches.
- Never give full system access to a single person. Aside from data breaches, sometimes it is possible to lose an entire organization to a phishing attack, as in the case of Code Source. Make sure no one person has full authorization and credentials in their possession to take down an entire company.
- Training and self-education. You can save yourself a major headache if you know what to do. Make sure to read and educate yourself about social engineering techniques and nuances, and have a plan if you ever fall victim to one. In cybersec, knowledge is power!
Recent phishing trends call for awareness
Phishing has been steadily rising over the past years, most notably during COVID-19. New forms of social engineering are on a constant rise as well because people are the easiest and a nearly exclusive way past any security framework.
The only way to avoid and defend from phishing attacks is by gaining awareness through self-educating and undergoing cybersecurity training. In our blog, you can learn more about your online security and privacy, how to protect yourself and stay safe when surfing the web.



